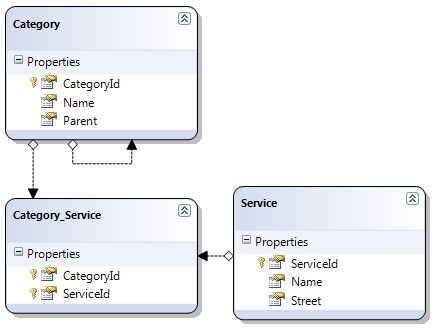
Ok, reinventing the wheel every time you build an application works great, as long as you aren't on a very very tight schedule. So due to time constraints (and my reluctance for spending time) I figured out this time I'll stick to standard ASP.NET role based security.
I never really bothered with trying, mainly because I usually had complex security built into my data structure (like individual access rights for different records).
So, obviously there is a way to do this with custom ASP.NET security providers, but doing security on my own saved me messing around with doing custom ASP.NET security.
So, this time I figured out, doing custom ASP.NET security isn't going to happen. Obviously there is only one administration website that needs authentication all over the place with no special roles and other fancy stuff. Just some plain .htaccess like security on a file-level basis.
.htaccess isn't the most scaleable solution (and quite impractical on IIS ;)) so I just started off by following the quite simple walkthrough on MSDN.
Now, after doing the user-creation you just need to drag the Login-Control onto your design surface and the user is presented with a pretty nice looking login form:
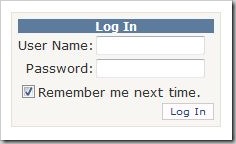 So, obviously this saves time. I don't need to drag 5 controls to the surface, I don't need to build some fancy cookie-login stuff for my application and the whole thing works. Great isn't it?
So, obviously this saves time. I don't need to drag 5 controls to the surface, I don't need to build some fancy cookie-login stuff for my application and the whole thing works. Great isn't it?
Now, where this really shines is when you try to access a folder that ASP.NET security was configured to deny. You get redirected to the Login.aspx file and the Log In control automatically handles redirection to the previously requested page etc.
Now, that's it basically. ASP.NET comes packed with loads of great tools that do authentication for you. Like password recovery dialogs, change password dialogs, create user wizard, login name display etc.
This all combined gives you a very solid toolset to work on from a programming and security perspective.